Cybersecurity is a daily struggle for business. Companies need to be alert to the hacks and data breaches that are becoming increasingly common. Windows 10 is driven on security. Since its release various solutions have been developed to help reduce the attack surface of a device. These solutions are constantly evolving to address the rapid changes in an always-connected world.
Businesses need to start thinking clever with their security strategy. They also have to assume defenses may be breached. Rather than focusing solely on how to prevent a breach, think how they can detect and remediate any security problem.
Windows Device Health Attestation (DHA) was introduced in the first release of Windows 10. It will ascertain if the modern security features are enabled while a system boots. It will then allow access to protected resources only if the device passes the health attestation. To do this it uses the Trusted Platform Module (TPM) chip.
In a nutshell, DHA sends data from a device’s boot process to a remote or on-premises health attestation service. This data is then checked by the DHA service to determine if any changes have been made on the device.
DHA integrates with the Windows 10 Mobile Device Management (MDM) framework. It works with devices that support Trusted Module Platform (TPM) 1.2 or 2.0 provisioned in firmware or discrete mode. DHA allows enterprises to raise the security bar to hardware monitored and attested security for on-premises devices. The devices can be:
- Managed by Active Directory
- Hybrid managed with both Active Directory and Azure Active Directory
- Managed via Azure Active Directory on managed cloud-based devices
A DHA policy checks the following boot configuration or attributes:
- Secure Boot
- BitLocker
- Early Launch AntiMalware (ELAM)
- Code integrity
The MDM solution enforces policy and uses the DHA report data sent back from the DHA service to enable any remedial action. It could check if BitLocker is enabled, if ELAM is protecting the device at the boot stage, or if Secure Boot is enabled and that the boot loader is not tampered with.
Managing DHA with ConfigMgr
Microsoft System Center Configuration Manager (ConfigMgr) can be used to manage Device Health Attestation. It can talk to either the remote DHA service managed by Microsoft, or an on-premises DHA service.
To configure on-premises DHA, Windows Server 2016 is required as a minimum prerequisite, along with three certificates—a DHA SSL, signing and encryption certificate—and a Windows 10 client with a TPM 1.2 or 2.0 chip in a clear/ready state.
For details on how to set up and configure the on-premises DHA service take a look at this Microsoft document titled Install and configure the DHA service on Windows Server 2016.
To manage DHA in ConfigMgr, a client setting needs to be enabled under \Administration\Overview\Client Settings. It is always recommended to use a custom client setting to define this.
If using the remote DHA service, in the Computer Agent setting Enable communication with Health Attestation Service needs to be set to Yes.
If using an on-premises DHA service, then the client setting Use on-premises Health Attestation Service needs to be set to Yes.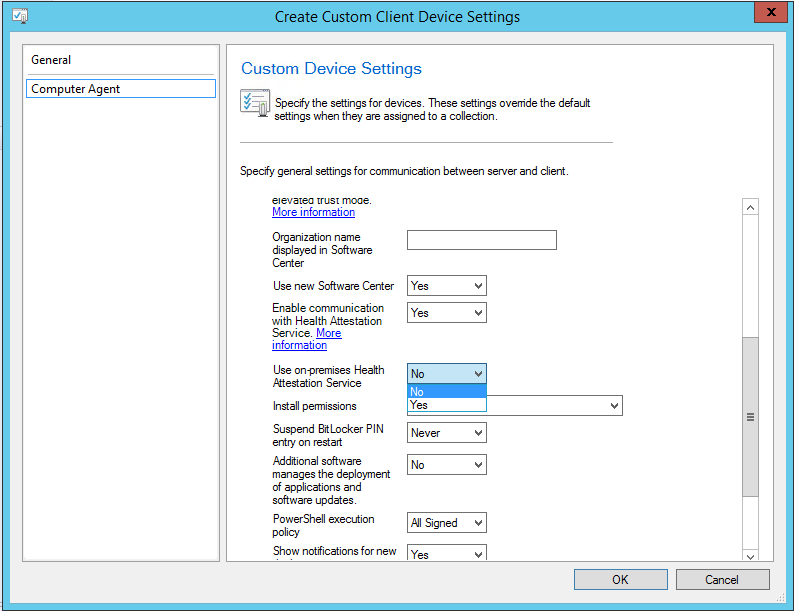
To enable the DHA service communication on a client device for on premises, starting with ConfigMgr 1702, the on-premises DHA URL needs to be configured on management points to support internal devices that do not have Internet access.
In the Administration\Overview\Site Configuration\Sites node, right-click the site server hosting the Management Point and select Configure site components\Management Point. In the Management Point Component Properties window, select the Advanced Options tab.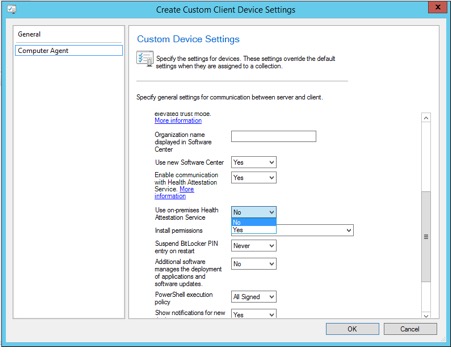
Click the Add button and enter the on-premises DHA URL.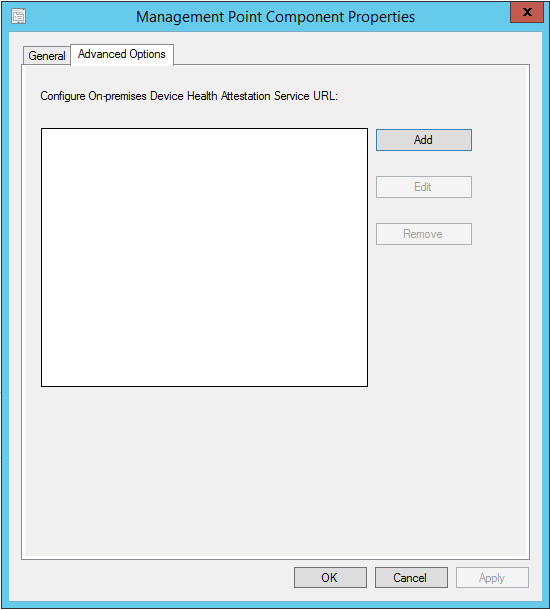
If your ConfigMgr site is pre-1702, first note that you are out of support and should be upgrading your site to get back on board as a supported concern. Second, note that the on-premises URL, which was previously populated in the client settings, will be migrated over to the management point properties. This is a nice piece of work by the ConfigMgr product group who are striving to make the upgrade process seamless and less painful.
With the relevant client settings and configuration in place, devices need to be targeted with the client agent settings so that they will start to report their health attestation.
As with all uber cool ConfigMgr features, DHA has its own donut-based dashboard which is located under the \Monitoring\Overview\Security\Device Health Attestation node.
The DHA dashboard reports on:
- Health Attestation Status. Displays devices in compliant, non-compliant, error, and unknown states.
- Devices Reporting Health Attestation. Displays a percentage of devices reporting their DHA status.
- Non-compliant Devices by Client Type. Displays devices which are non-compliant
- Top Missing Health Attestation Settings. Displays the number of devices which are missing the DHA setting.
If you are a fan of traditional ConfigMgr reports, then you are in luck. Under \Monitoring\Overview\Reporting\Reports\Device Management is the report List of devices by Health Attestation state.
With this report, you can be granular about which DHA attribute you wish to report on, for example devices with BitLocker not enabled.
Closing Thoughts
With Windows 10 the bar has been set for feature rich security solutions, with plenty of choice on which to implement (as many as possible) and ConfigMgr makes the management of them a breeze. Why not take advantage of the Window Device Health Attestation service and make your businesses security implementation more proactive than reactive?




