ConfigMgr has many little gems tucked away, underutilized, forgotten at times. Configuration Items (CI) is one of these gems.
CI’s have been around since Microsoft System Center Configuration Manager (ConfigMgr) 2007 days, when they were known as Desired State Configuration. Configuration Items are created, set to a Configuration Baseline (CB) which is then deployed to a collection. Compliance is evaluated against the baseline and reported back to ConfigMgr. Non-compliance can be remediated to bring devices back into a compliant state – super cool, super powerful and really easy to set up.
A CI can be created using different item types. These range from registry, file system, Active Directory query, WQL query, WMI query to a script and a CB can contain one or more CI’s to add power and flexibility to the evaluation.
Cis can be created for Window servers and clients, and Mac OS X systems with a ConfigMgr client installed. CIs can be deployed to MDM devices which aren’t running a ConfigMgr client. (Note that as of August 14, 2018, hybrid mobile device management is a deprecated feature of ConfigMgr).
The Configuration Item itself stores information based on the following:
- Detection method information. This is required if the configuration item contains applications settings. A checkbox for this is enabled during the CI wizard.
- Settings. The settings contain the conditions that need to be assessed for compliance on device.
- Compliance rules. These contain the conditions that exist to check compliance against a device.
- Supported platforms. These are the platforms against which the compliance is assessed. If the platform matches the one selected, then evaluation can take place.
Creating your first Configuration Item
Let’s create a CI to get a feel for the information that can be assigned during the configuration item wizard.
CI’s can be created in the ConfigMgr console from the location \Assets and Compliance\Overview\Compliance Settings by right-clicking Configurations Items and selecting Create Configuration Item.
In the General section of wizard, a name for the CI must be entered. A choice of supported platforms is available, as previously mentioned. CI’s can be categorized, like drivers, so they can be easily searched for and filtered.
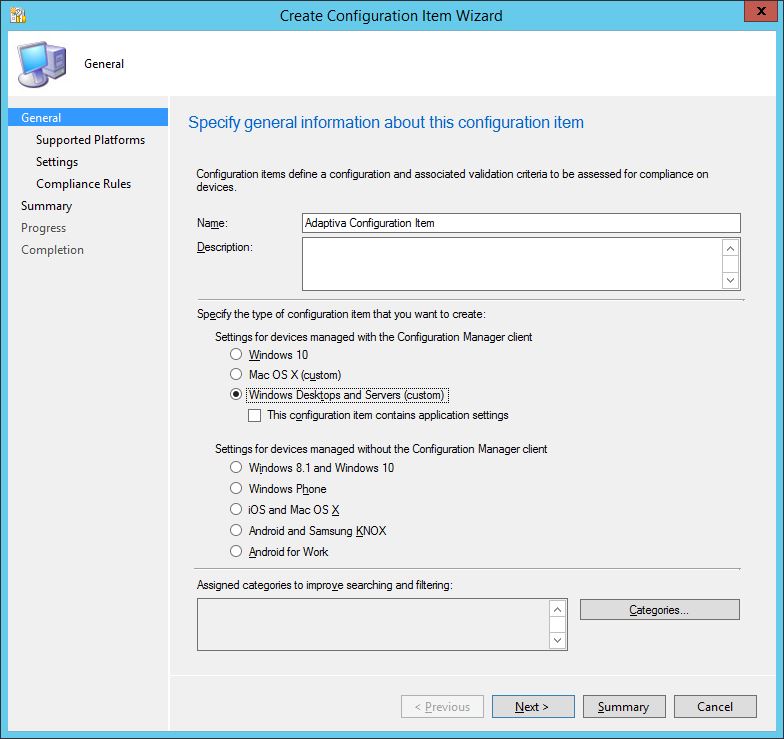
On the Supported Platform screen, granular selection of the platform type can be performed. Since I had chosen to create the CI for Windows Desktop and Servers (Custom), I have a choice of various operating systems to target the CI at. For this example, I have narrowed down my choice to just Windows 10 x64 device types.
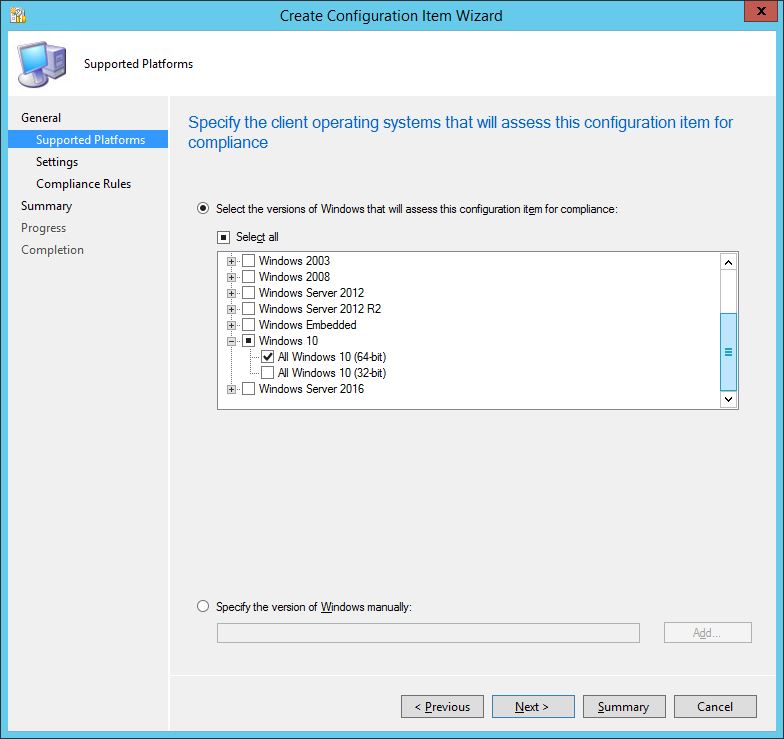
Now we can start to build up the required compliance rules. Clicking New will launch the Setting window.
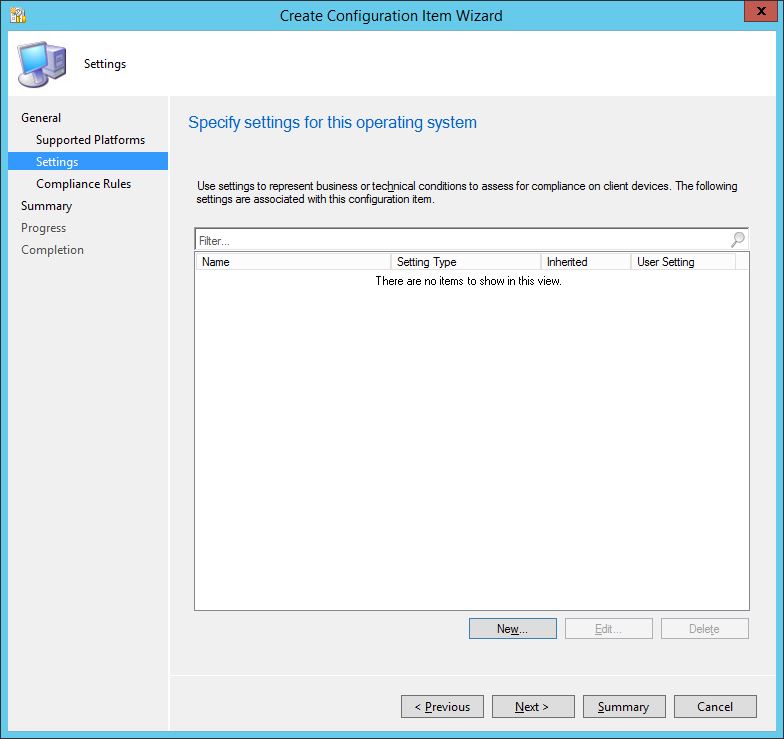
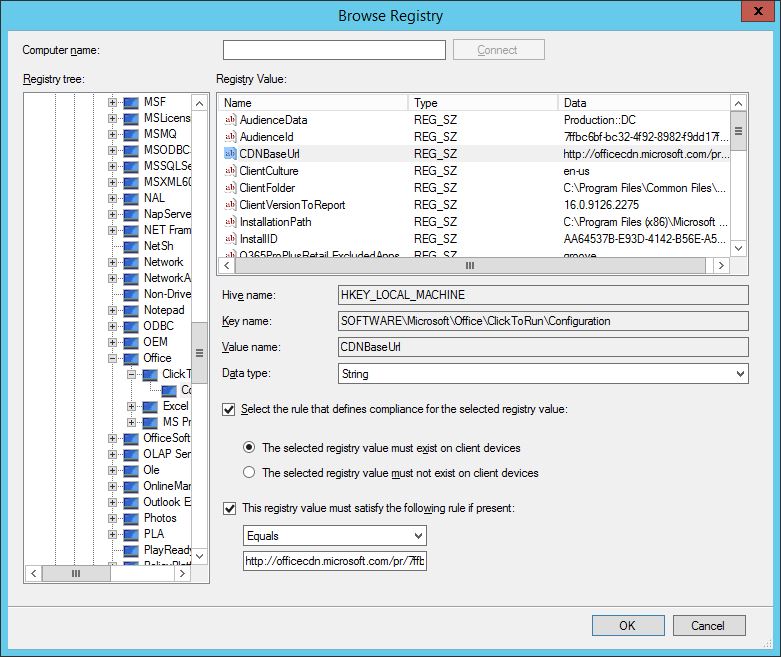
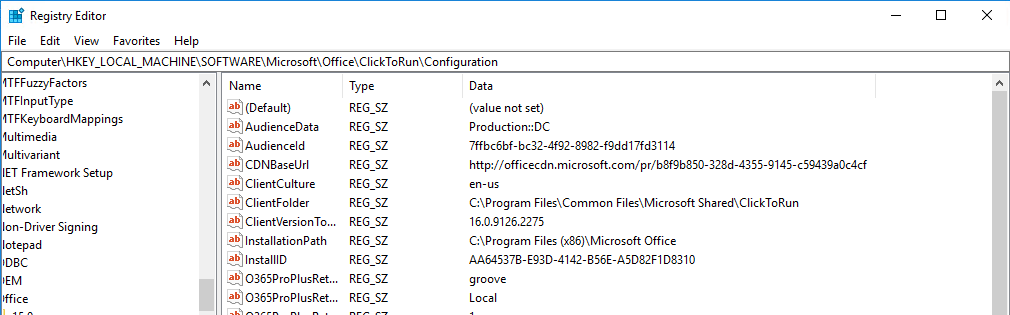
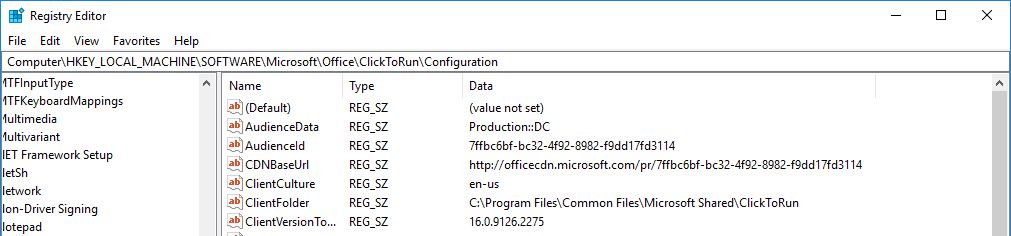
The full set of setting types are available to choose from. For the example I’m going to choose a Registry value type. I want to check the registry value for the Office 365 update channel on my client devices and remediate any that are not using the Semi Annual Channel CDNBaseURL http://officecdn.microsoft.com/pr/7ffbc6bf-bc32-4f92-8982-f9dd17fd3114. This is set in the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration\CDNBaseUrl.
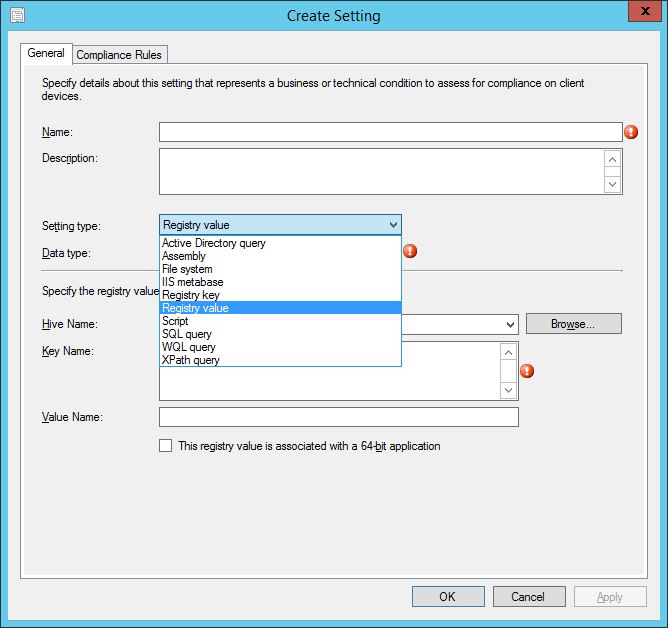
By browsing a local or remote device, the exact details required can be collated simply and effectively.
The CI and the compliance rules are created with minimum fuss.
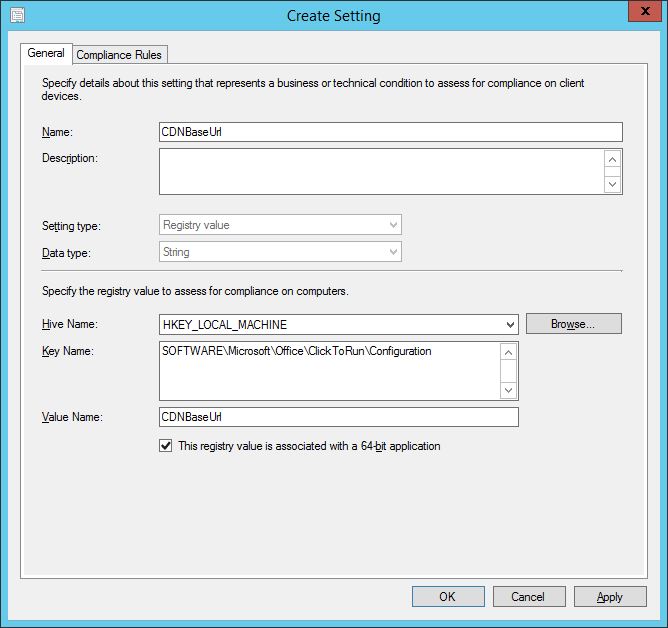
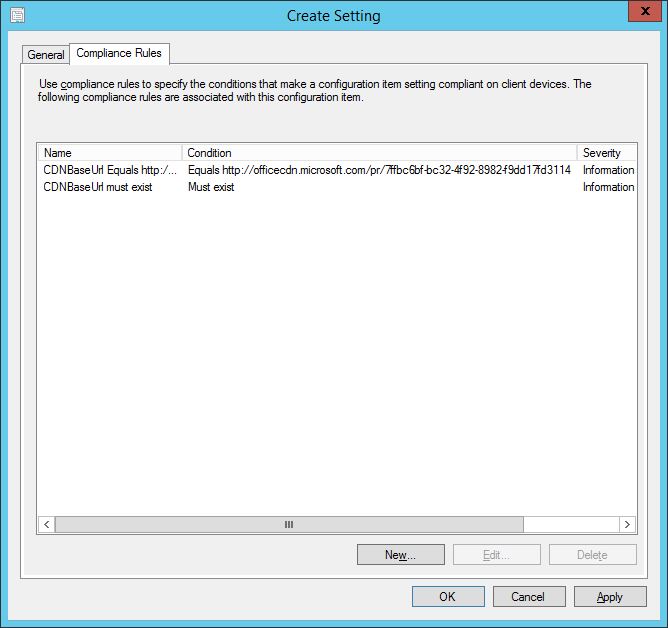
In the Compliance Rules tab, conditions can be set to be remediated. Double-clicking one of the defined conditions brings up the dialog window which enables you to do this. In my example, I have checked the box to Remediate noncompliant rules when supported for the CDNBaseURL.
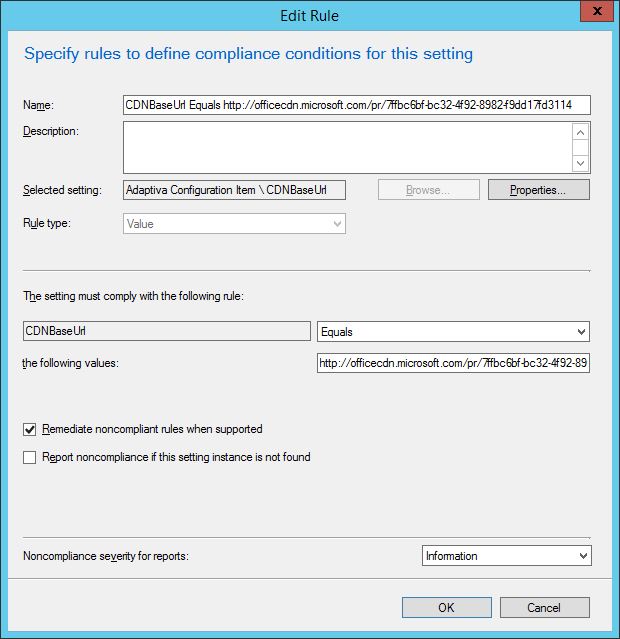
With the CI configured, it’s time to create the baseline for deployment to targeted devices.
Configuring the Configuration Baseline for deployment to devices.
In the console, navigate to \Assets and Compliance\Overview\Compliance Settings\Configuration Baselines, right-click and select Create Configuration Baseline.
Give the CB a name and choose Configuration Items from the Add drop down.
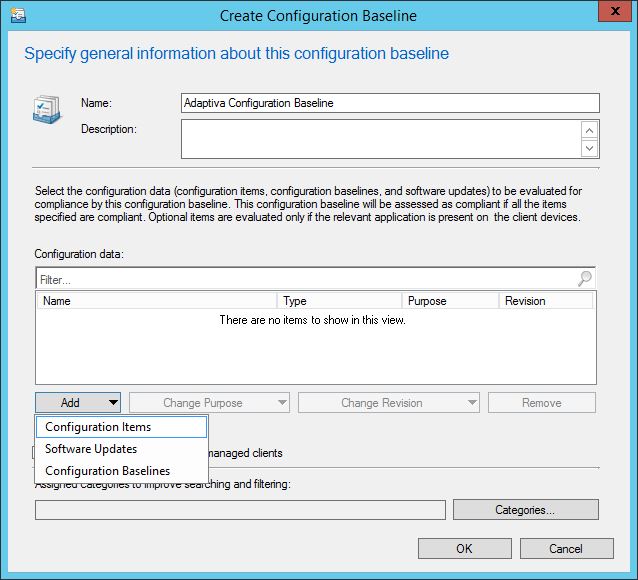
Now it’s a simple case of selecting the CI created previously and adding it to the baseline.
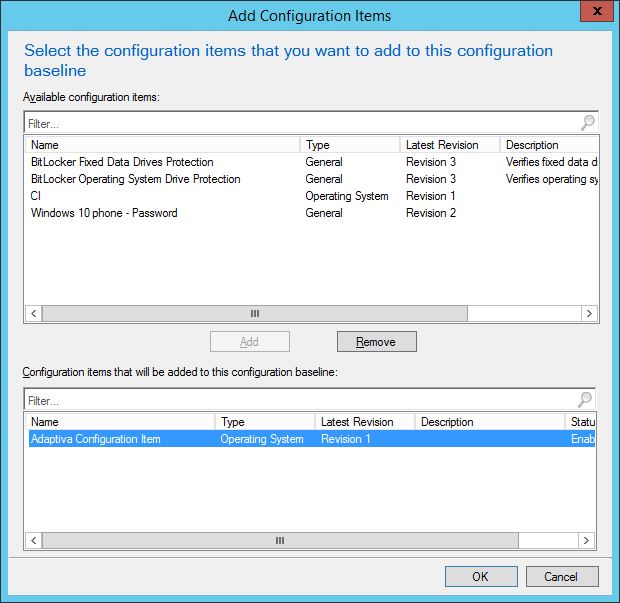
Next up, we can set a schedule for the compliance evaluation of the baseline. Use this sensibly, you don’t want to impact SCCM performance with overzealous schedules. Also, set to remediate. If the collection being targeted has a maintenance window, allow remediation outside the window. With the baseline set, the CB is deployed to a collection.
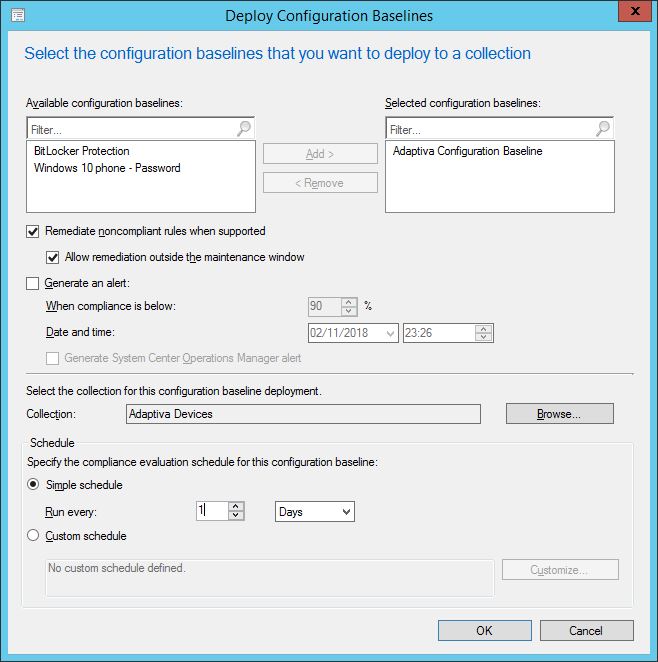
A little-known feature is the ability to right-click a baseline deployment and create collections of devices that are either Compliant, Error, Non-compliant or Unknown. This is a super handy feature.
Let’s see what happens on a targeted device which isn’t running in the Semi Annual Channel. By using the CI baseline, I can set this to flip into the Semi Annual and therefore become compliant which is how I want to deploy Office 365 in my environment.
As you can see, the device is currently set with CDNBaseURL http://officecdn.microsoft.com/pr/b8f9b850-328d-4355-9145-c59439a0c4cf, which is the Semi Annual Channel (targeted) URL.
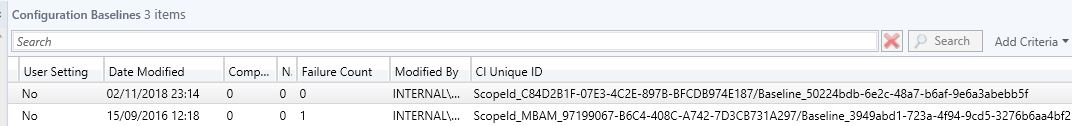
In the SCCM console, take note of the CI Unique ID for the baseline you create. You may need to add this column to be able to see it.
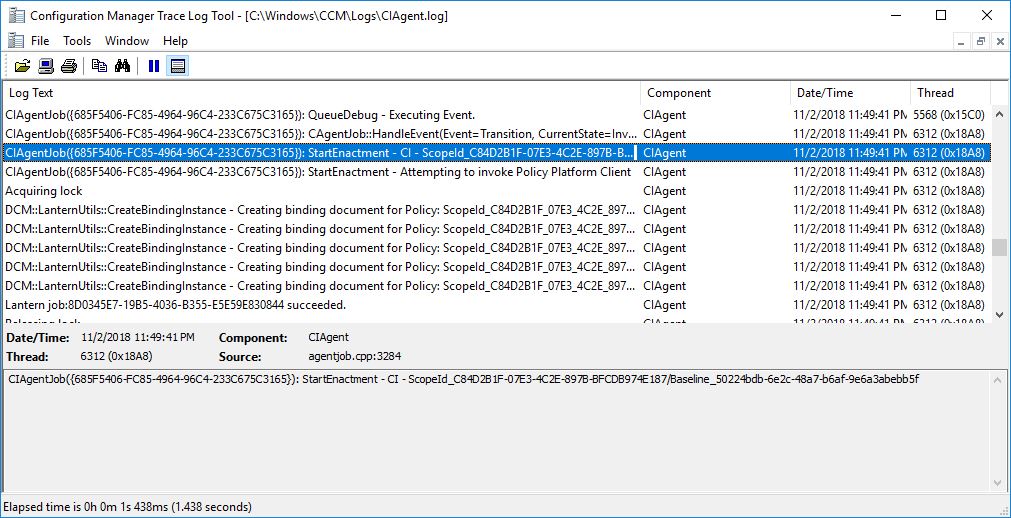
When policy is run, you will see that the processing of the baseline takes place by checking in the CIAgent.log.
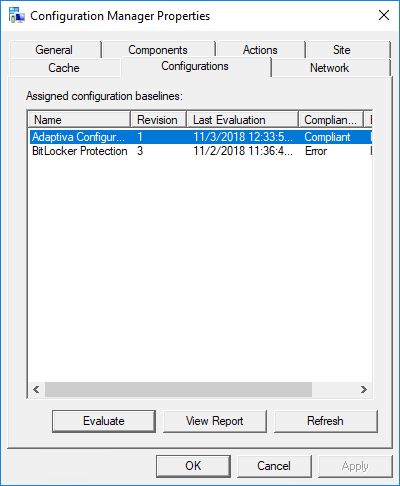
When your CI and baseline are not set to remediate then the device will report back as non-compliant, if this is not set to the registry value you want for a compliant state to be achieved. In the ConfigMgr applet in the Control Panel, you will see a Non-Compliant state reported in the Configurations tab.
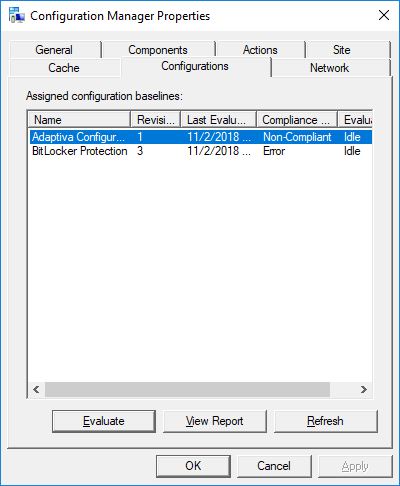
You can click the report to see the full details of the compliance check.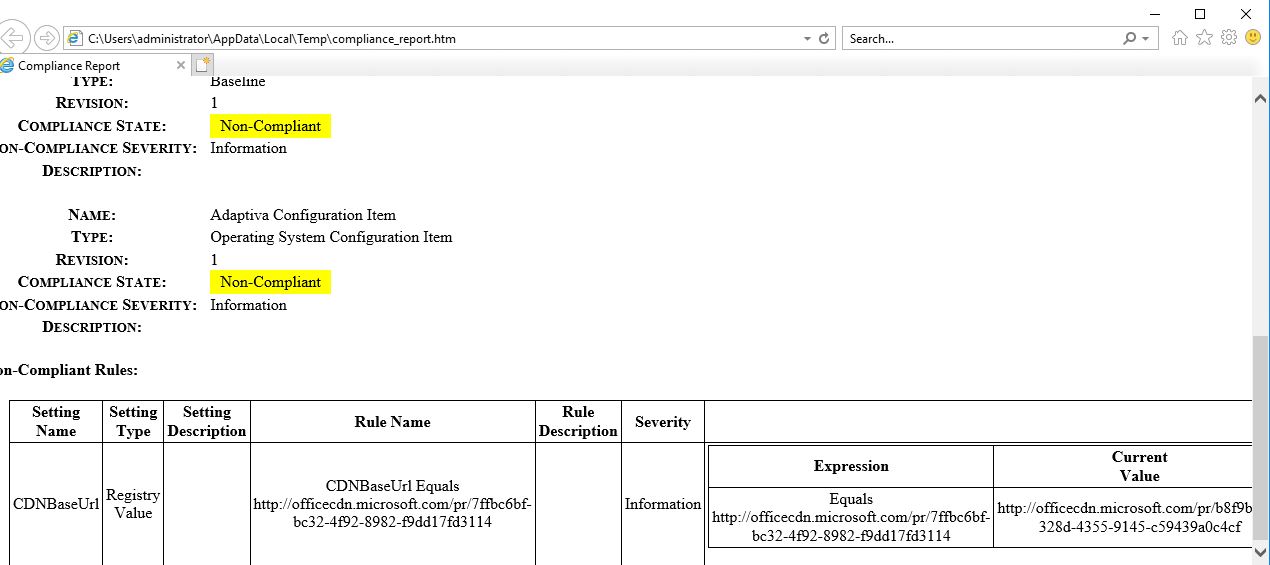
With remediation set on the CI and baseline, the device will be updated to enforce compliance.
As you can see the registry value is updated to reflect the desired state.
Having run through the overview of setting up a CI and CB, why not dig deeper by creating a script CI and associated remediation script. Or you could create a child configuration item which inherits the original configuration from the parent configuration item. How about creating a configuration baseline from a defined set of software updates, and reporting back on their compliance? The power of Configuration Items and Baselines is at your fingertips.
Obviously in today’s security-conscious world, maintaining a consistent maintaining consistent configuration crucial. Windows 10 gives you many more options and settings than you had to know in Windows 7/8/8.1. If you’d like to learn what ConfigMgr can do for security beyond CI’s you might want to check out a new report of I’ve written, Managing Windows 10 Security using ConfigMgr.




